A firewall administrator wants to be able at to see all NAT sessions that are going ‘through a firewall with source NAT. Which CLI command can the administrator use?
A. show session all filter nat-rule-source
B. show running nat-rule-ippool rule "rule_name
C. show running nat-policy
D. show session all filter nat source
A superuser is tasked with creating administrator accounts for three contractors. For compliance purposes, all three contractors will be working with different device-groups in their hierarchy to deploy policies and objects. Which type of role-based access is most appropriate for this project?
A. Create a Dynamic Read only superuser
B. Create a Dynamic Admin with the Panorama Administrator role
C. Create a Device Group and Template Admin
D. Create a Custom Panorama Admin
Explanation: Custom Panorama Admin: Custom Panorama Admin roles allow you to customize the elements of Panorama that an administrator can access. You can hide tabs in the web interface, you can set specific items in Panorama to read-only, or you can limit an administrator’s access to Panorama plugins. Custom Panorama Admin roles require planning and configuration, but they provide extensive flexibility because you can control what administrators can access through the web interface or the CLI. Device Group and Template Admin: Device Group and Template Admin roles also require configuration because there are no built-in examples. These Admin Roles allow you to define which Panorama templates or Panorama device groups an administrator can access and configure. You can hide tabs in the web interface or set specific items to read only to control what administrators can configure.
What would allow a network security administrator to authenticate and identify a user with a new BYOD-type device that is not joined to the corporate domain?
A. an Authentication policy with 'unknown' selected in the Source User field
B. an Authentication policy with 'known-user' selected in the Source User field
C. a Security policy with 'known-user' selected in the Source User field
D. a Security policy with 'unknown' selected in the Source User field
Explanation: For a network security administrator to authenticate and identify a user with a
new BYOD-type device that is not joined to the corporate domain, the most effective
method is to use an Authentication policy targeting users not yet identified by the system.
A. an Authentication policy with 'unknown' selected in the Source User field:
An Authentication policy allows the firewall to challenge unidentified users for
credentials. By selecting 'unknown' in the Source User field, the policy targets
users who have not yet been identified by the firewall, which would include users
on new BYOD devices not joined to the domain.
Once the user provides valid credentials, the firewall can authenticate the user and
map their identity to subsequent sessions, enabling the application of user-based
policy rules and monitoring.
This approach ensures that new and unknown devices can be properly authenticated and
identified without compromising security or requiring the device to be part of the corporate
domain.
Which GloDalProtecI gateway setting is required to enable split-tunneting by access route, destination domain and application?
A. Tunnel mode
B. Satellite mode
C. IPSec mode
D. No Direct Access to local networks
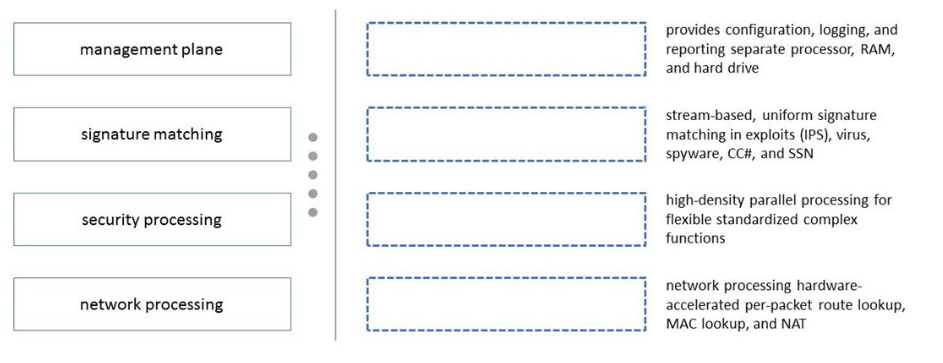
Please match the terms to their corresponding definitions.
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits. Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
A. Use RSA instead of ECDSA for traffic that isn't sensitive or high-priority.
B. Use the highest TLS protocol version to maximize security.
C. Use ECDSA instead of RSA for traffic that isn't sensitive or high-priority.
D. Use SSL Forward Proxy instead of SSL Inbound Inspection for decryption.
Explanation: Decryption can be resource-intensive, and in scenarios where the firewall is
nearing its resource limits, optimizing decryption practices is crucial. One way to do this is
by choosing more efficient encryption algorithms that require less computational power.
C. Use ECDSA instead of RSA for traffic that isn't sensitive or high-priority:
Elliptic Curve Digital Signature Algorithm (ECDSA) is known for requiring smaller
key sizes compared to RSA for a comparable level of security. This translates to
less computational overhead during the encryption and decryption processes.
By using ECDSA for traffic that isn't sensitive or high-priority, the administrator can
reduce the processing load associated with decryption on the firewall. This is
particularly beneficial in scenarios where resource optimization is necessary.
It's important to note that this approach does not compromise the security of
encrypted traffic. Instead, it offers a more resource-efficient way to manage
decryption, thus helping to maintain firewall performance even when system
resources are under significant demand.
By judiciously applying this strategy, administrators can manage the decryption workload
on the firewall, ensuring continued protection and inspection of encrypted traffic without
overburdening the firewall's resources.
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
A. Log Collector
B. Panorama
C. Legacy
D. Management Only
An engineer is troubleshooting a traffic-routing issue. What is the correct packet-flow sequence?
A. PBF > Zone Protection Profiles > Packet Buffer Protection
B. BGP > PBF > NAT
C. PBF > Static route > Security policy enforcement
D. NAT > Security policy enforcement > OSPF
Explanation: The correct packet-flow sequence is C. PBF > Static route > Security policy enforcement. This sequence describes the order of operations that the firewall performs when processing a packet. PBF stands for Policy-Based Forwarding, which is a feature that allows the firewall to override the routing table and forward traffic based on the source and destination addresses, application, user, or service. PBF is evaluated before the static route lookup, which is the default method of forwarding traffic based on the destination address and the longest prefix match. Security policy enforcement is the stage where the firewall applies the security policy rules to allow or block traffic based on various criteria, such as zone, address, port, user, application, etc.
| Page 3 out of 41 Pages |
| Previous |