Review the screenshots.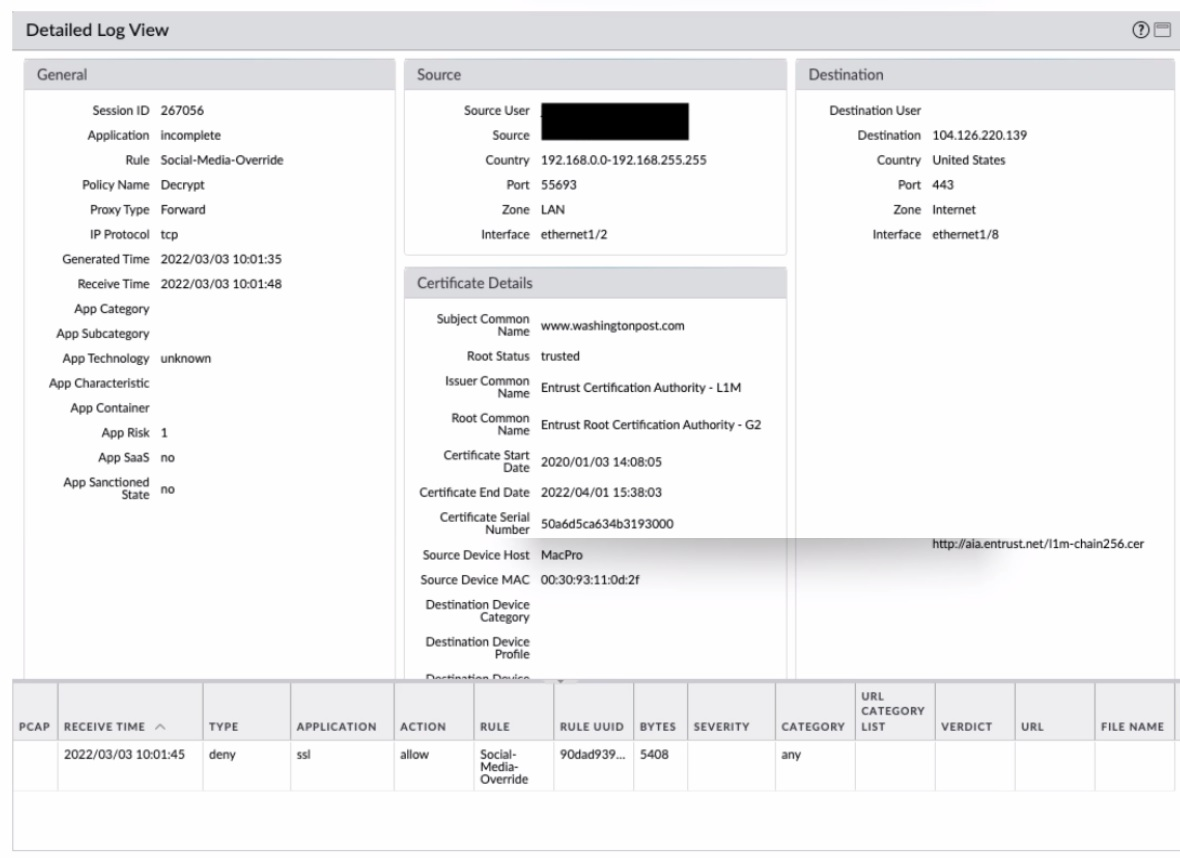
What is the most likely reason for this decryption error log?
A. The Certificate fingerprint could not be found.
B. The client expected a certificate from a different CA than the one provided.
C. The client received a CA certificate that has expired or is not valid.
D. Entrust is not a trusted root certificate authority (CA).
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama?
A. A User-ID Certificate profile must be configured on Panorama.
B. The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
C. User-ID Redistribution must be configured on Panorama to ensure that all firewalls have the same mappings.
D. A master device with Group Mapping configured must be set in the device group where the Security rules are configured.
Explanation: When building Security rules in a Device Group that need to allow traffic to
specific users and groups defined in Active Directory, it's essential to have user and group
information available in Panorama to select these entities for the rules.
D. A master device with Group Mapping configured must be set in the device group
where the Security rules are configured:
The concept of a "master device" in Panorama refers to a specific firewall that is
designated to provide certain settings or information, such as user and group
mappings from Active Directory, to Panorama. This information can then be used
across other firewalls within the same device group.
By configuring Group Mapping on a master device, Panorama can leverage this
information to populate user and group objects. These objects can then be used in
Security rules within the device group, allowing for the creation of policies that are
based on user identity and group membership, as defined in Active Directory.
This setup ensures that Panorama has the necessary context to apply user- and
group-based policies accurately across the managed firewalls, facilitating
centralized management and consistency in policy enforcement.
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment. Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
A. Kerberos or SAML authentication need to be configured
B. LDAP or TACACS+ authentication need to be configured
C. RADIUS is only supported for a transparent Web Proxy.
D. RADIUS is not supported for explicit or transparent Web Proxy
Explanation: For explicit Web Proxy deployment on PAN-OS, Palo Alto Networks currently supports Kerberos and SAML as authentication methods. RADIUS is not supported for explicit or transparent Web Proxy authentication on Palo Alto Networks appliances, which means that if the client is currently using RADIUS, they will need to configure an alternate supported authentication method. LDAP or TACACS+ authentication is not directly supported for Web Proxy authentication in PAN-OS.For more information on supported Web Proxy authentication methods, please refer to the latest Palo Alto Networks "PANOS ® Web Interface Reference Guide".
An engineer is configuring a firewall with three interfaces:
A. Set DNS and Palo Alto Networks Services to use the ethernet1/1 source interface.
B. Set DNS and Palo Alto Networks Services to use the ethernet1/2 source interface.
C. Set DNS and Palo Alto Networks Services to use the MGT source interface.
D. Set DDNS and Palo Alto Networks Services to use the MGT source interface.
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing. What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
A. Add the Evernote application to the Security policy rule, then add a second Security policy rule containing both HTTP and SSL.
B. Create an Application Override using TCP ports 443 and 80.
C. Add the HTTP. SSL. and Evernote applications to the same Security policy
D. Add only the Evernote application to the Security policy rule.
Explanation: To create an application-based Security policy rule to allow Evernote, the administrator only needs to add the Evernote application to the Security policy rule. The Evernote application is a predefined App-ID that identifies the traffic generated by the Evernote client or web interface. The Evernote application implicitly uses SSL and web browsing as dependencies, which means that the firewall automatically allows these applications when the Evernote application is allowed. Therefore, there is no need to add HTTP, SSL, or web browsing applications to the same Security policy rule. Adding these applications would broaden the scope of the rule and potentially allow unwanted traffic. References: App-ID Overview, Create a Security Policy Rule
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1. In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
A. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Source Translation: Static IP / 172.16.15.1
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Trust -
Destination IP: 172.16.15.10 -
Application: ssh
B. NAT Rule:
Source Zone: Trust -
Source IP: 192.168.15.0/24 -
Destination Zone: Trust -
Destination IP: 192.168.15.1 -
Destination Translation: Static IP / 172.16.15.10
Security Rule:
Source Zone: Trust -
Source IP: 192.168.15.0/24 -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
C. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Trust -
Destination IP: 192.168.15.1 -
Destination Translation: Static IP /172.16.15.10
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
D. NAT Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Source Translation: dynamic-ip-and-port / ethernet1/4
Security Rule:
Source Zone: Trust -
Source IP: Any -
Destination Zone: Server -
Destination IP: 172.16.15.10 -
Application: ssh
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
A. No Direct Access to local networks
B. Tunnel mode
C. iPSec mode
D. Satellite mode
An engineer is deploying multiple firewalls with common configuration in Panorama. What are two benefits of using nested device groups? (Choose two.)
A. Inherit settings from the Shared group
B. Inherit IPSec crypto profiles
C. Inherit all Security policy rules and objects
D. Inherit parent Security policy rules and objects
| Page 5 out of 41 Pages |
| Previous |