Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
A. Perform packet forwarding to the active-passive peer during session setup and asymmetric traffic flow.
B. Perform synchronization of routes, IPSec security associations, and User-ID information.
C. Perform session cache synchronization for all HA cluster members with the same cluster ID.
D. Perform synchronization of sessions, forwarding tables, and IPSec security associations between firewalls in an HA pair.
Explanation: In a High Availability (HA) configuration, particularly in an active-passive setup, it's crucial that the passive unit is kept up to date with the current state of the active
unit. This ensures a seamless transition in the event of a failover. The HA4 interface is
dedicated to this synchronization task.
D. Perform synchronization of sessions, forwarding tables, and IPSec security
associations between firewalls in an HA pair:
The HA4 interface is responsible for the synchronization of critical stateful
information between the active and passive units in an HA pair. This includes
session information, ensuring that the passive unit can continue existing sessions
without interruption if it needs to become active.
In addition to session information, HA4 also synchronizes forwarding tables, which
contain information on how to route packets, and IPSec security associations,
which are necessary for maintaining secure VPN tunnels.
This synchronization ensures that both units in an HA pair have identical information
regarding the current state of the network, sessions, and security associations, enabling a
smooth and immediate transition to the passive unit in case the active unit fails.
Information Security is enforcing group-based policies by using security-event monitoring
on Windows User-ID agents for IP-to-User mapping in the network. During the rollout,
Information Security identified a gap for users authenticating to their VPN and wireless
networks.
Root cause analysis showed that users were authenticating via RADIUS and that
authentication events were not captured on the domain controllers that were being
monitored Information Security found that authentication events existed on the Identity
Management solution (IDM). There did not appear to be direct integration between PANOS
and the IDM solution.
How can Information Security extract and learn iP-to-user mapping information from
authentication events for VPN and wireless users?
A. Add domain controllers that might be missing to perform security-event monitoring for VPN and wireless users.
B. Configure the integrated User-ID agent on PAN-OS to accept Syslog messages over TLS.
C. Configure the User-ID XML API on PAN-OS firewalls to pull the authentication events directly from the IDM solution
D. Configure the Windows User-ID agents to monitor the VPN concentrators and wireless controllers for IP-to-User mapping.
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
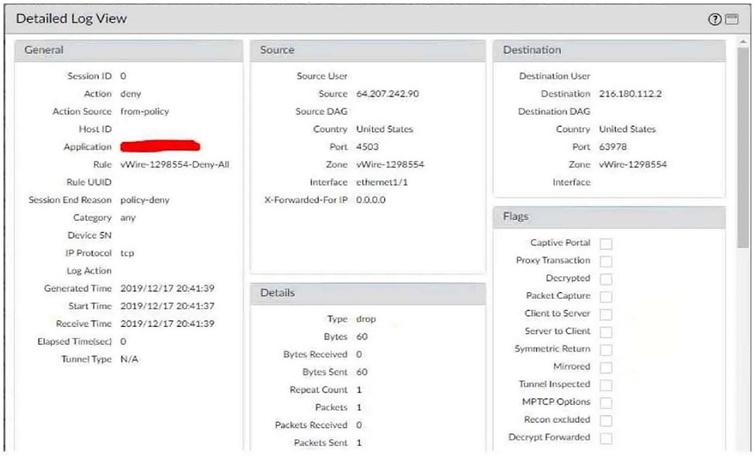
A. Incomplete
B. unknown-tcp
C. Insufficient-data
D. not-applicable
Explanation: Traffic didn't match any other policies and so landed at the implicit "deny all" policy. If it's deny all, the traffic was dropped before the application could be determined.
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed. Which set of actions should the engineer take to achieve this goal?
A. 1- Open the current log forwarding profile.
2. Open the existing match list for threat log type.
3. Define the filter.
4. Select the syslog forward method.
B. 1. Create a new log forwarding profile.
2. Add a new match list for threat log type.
3. Define the filter.
4. Select the Panorama and syslog forward methods.
C. 1. Open the current log forwarding profile.
2. Add a new match list for threat log type.
3. Define the filter.
4. Select the syslog forward method.
D. 1. Create a new log forwarding profile.
2. Add a new match list for threat log type.
3. Define the filter.
4. Select the syslog forward method.
What does the User-ID agent use to find login and logout events in syslog messages?
A. Syslog Server profile
B. Authentication log
C. Syslog Parse profile
D. Log Forwarding profile
An engineer decides to use Panorama to upgrade devices to PAN-OS 10.2. Which three platforms support PAN-OS 10.2? (Choose three.)
A. PA-220
B. PA-800 Series
C. PA-5000 Series
D. PA-500
E. PA-3400 Series
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates. What must occur to have Antivirus signatures update?
A. An Antivirus license is needed first, then a Security profile for Antivirus needs to be created.
B. An Antivirus license must be obtained before Dynamic Updates can be downloaded or installed.
C. An Advanced Threat Prevention license is required to see the Dynamic Updates for Antivirus.
D. Install the Application and Threats updates first, then refresh the Dynamic Updates.
When configuring explicit proxy on a firewall, which interface should be selected under the Listening interface option?
A. ingress for the outgoing traffic to the internet
B. Loopback for the proxy
C. Firewall management
D. ingress for the client traffic
| Page 6 out of 41 Pages |
| Previous |