A network administrator wants to deploy SSL Forward Proxy decryption. What two attributes should a forward trust certificate have? (Choose two.)
A. A subject alternative name
B. A private key
C. A server certificate
D. A certificate authority (CA) certificate
An engineer needs to permit XML API access to a firewall for automation on a network segment that is routed through a Layer 3 sub-interface on a Palo Alto Networks firewall. However, this network segment cannot access the dedicated management interface due to the Security policy. Without changing the existing access to the management interface, how can the engineer fulfill this request?
A. Specify the subinterface as a management interface in Setup > Device > Interfaces.
B. Add the network segment's IP range to the Permitted IP Addresses list.
C. Enable HTTPS in an Interface Management profile on the subinterface
D. Configure a service route for HTTP to use the subinterface.
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules. How can this be achieved?
A. By configuring Data Redistribution Client in Panorama > Data Redistribution
B. By configuring User-ID group mapping in Panorama > User Identification
C. By configuring User-ID source device in Panorama > Managed Devices
D. By configuring Master Device in Panorama > Device Groups
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
A. NAT
B. DOS protection
C. QoS
D. Tunnel inspection
Exhibit.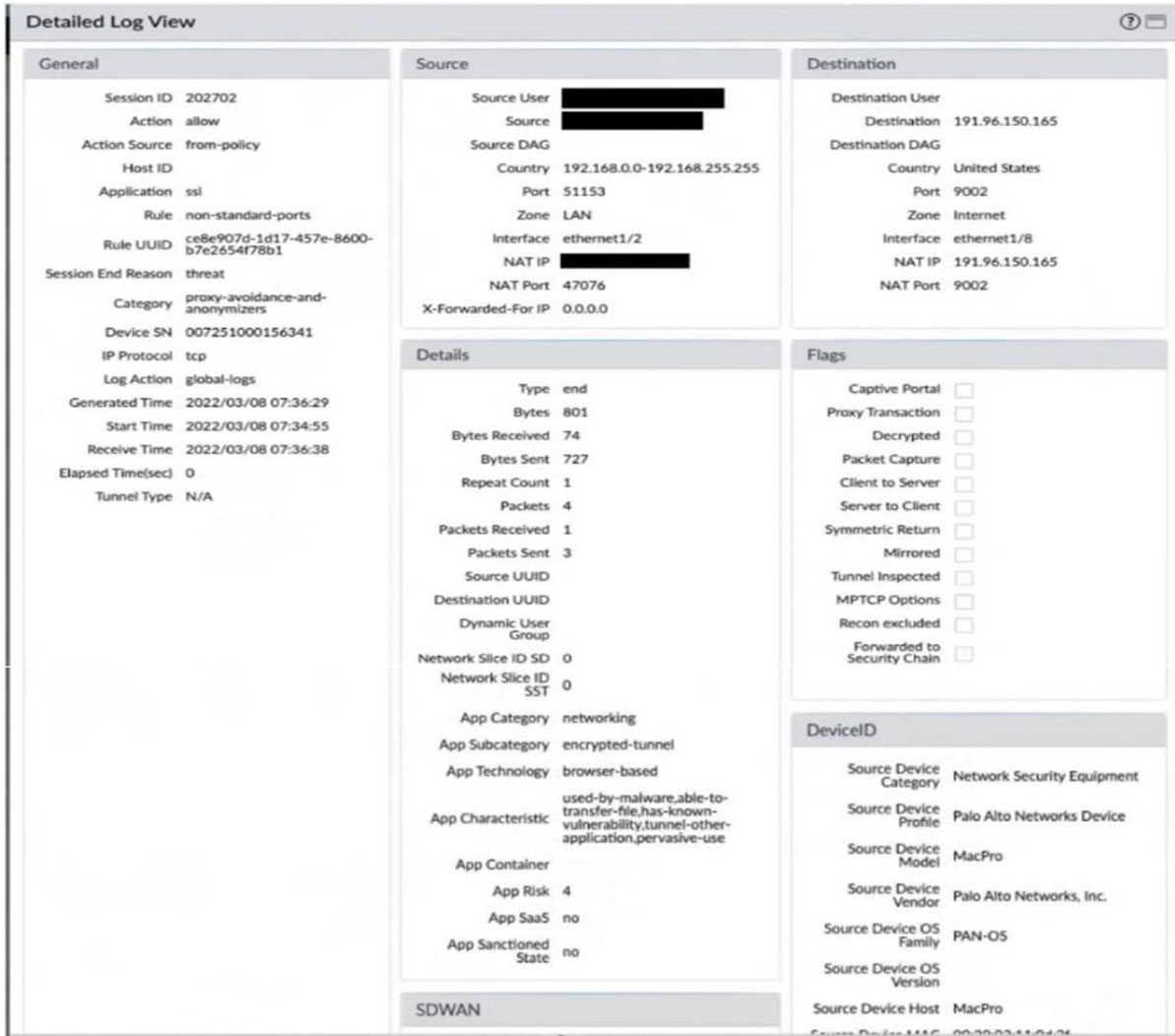
Given the screenshot, how did the firewall handle the traffic?
A. Traffic was allowed by profile but denied by policy as a threat.
B. Traffic was allowed by policy but denied by profile as a threat.
C. Traffic was allowed by policy but denied by profile as encrypted.
D. Traffic was allowed by policy but denied by profile as a nonstandard port.
An administrator needs to validate that policies that will be deployed will match the appropriate rules in the device-group hierarchy. Which tool can the administrator use to review the policy creation logic and verify that unwanted traffic is not allowed?
A. Preview Changes
B. Managed Devices Health
C. Test Policy Match
D. Policy Optimizer
An administrator notices interface ethernet1/2 failed on the active firewall in an active / passive firewall high availability (HA) pair Based on the image below what - if any - action was taken by the active firewall when the link failed?
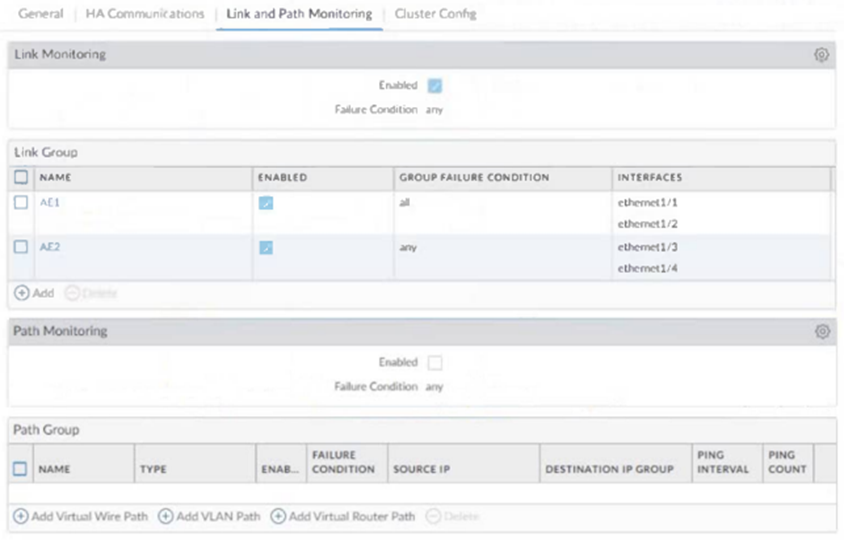
A. The active firewall failed over to the passive HA member because "any" is selected for the Link Monitoring
B. No action was taken because Path Monitoring is disabled
C. No action was taken because interface ethernet1/1 did not fail
D. The active firewall failed over to the passive HA member due to an AE1 Link Group failure
What must be configured to apply tags automatically based on User-ID logs?
A. Device ID
B. Log Forwarding profile
C. Group mapping
D. Log settings
| Page 7 out of 37 Pages |
| Previous |