An administrator is using Panorama to manage multiple firewalls. After upgrading all
devices to the latest PAN-OS software, the administrator enables log forwarding from the
firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to
Panorama?
A. Export the log database.
B. Use the import option to pull logs.
C. Use the scp logdb export command.
D. Use the ACC to consolidate the logs.
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
A. Traffic logs
B. Data filtering logs
C. Policy Optimizer
D. Wireshark
Explanation: To determine which sources an engineer can use to gather information about
application patterns for creating custom signatures, let’s analyze each option based on
PAN-OS 11.0 documentation and typical network troubleshooting practices.
A. Traffic Logs
Why It’s Correct:
How to Use:
Documentation Reference:
B. Data Filtering Logs
Why It’s Incorrect:
Documentation Reference:
C. Policy Optimizer
Why It’s Incorrect:
Documentation Reference:
D. Wireshark
Why It’s Correct:
How to Use:
Documentation Reference:
Summary of Correct Choices
Traffic Logs:
Wireshark:
Which two scripting file types require direct upload to the Advanced WildFire portal/API for analysis? (Choose two.)
A. Ps1
B. Perl
C. Python
D. VBS
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
A. OSPFV3
B. ECMP
C. ASBR
D. OSBF
A firewall administrator needs to check which egress interface the firewall will use to route the IP 10.2.5.3. Which command should they use?
A. test routing route ip 10.2.5.3 *
B. test routing route ip 10.2.5.3 virtual-router default
C. test routing fib-lookup ip 10.2.5.0/24 virtual-router default
D. test routing fib-lookup ip 10.2.5.3 virtual-router default
Explanation: To determine the egress interface a Palo Alto Networks firewall will use to route a specific IP address, the appropriate command is test routing fib-lookup ip 10.2.5.3 virtual-router default. This command performs a Forwarding Information Base (FIB) lookup for the specified IP address within the context of the specified virtual router, which in this case is the default virtual router. The FIB lookup process checks the routing table and the associated forwarding information to determine the next-hop and the egress interface for the given IP address. This command is instrumental for troubleshooting and verifying routing decisions made by the firewall to ensure that traffic is routed as expected through the network infrastructure.
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
A. Configure the decryption profile
B. Define a Forward Trust Certificate
C. Configure SSL decryption rules
D. Configure a SSL/TLS service profile
Explanation: To configure SSL Forward Proxy decryption on a Palo Alto Networks firewall,
certain key components must be set up to ensure secure and effective decryption and
inspection of SSL/TLS encrypted traffic:
B. Define a Forward Trust Certificate:
A Forward Trust Certificate is essential for SSL Forward Proxy decryption. This
certificate is used by the firewall to dynamically generate certificates for SSL sites
that are trusted. When the firewall decrypts and inspects the traffic and then re-encrypts
it, the new certificate presented to the client comes from the Forward
Trust Certificate authority. This certificate must be trusted by client devices, often
requiring the Forward Trust CA certificate to be distributed and installed on client
devices.
C. Configure SSL decryption rules:
SSL decryption rules are the policies that determine which traffic is to be
decrypted. These rules specify the source, destination, service, and URL category,
among other criteria. The rules define what traffic the SSL Forward Proxy will
apply to, enabling selective decryption based on security and privacy
requirements.
Together, these components form the basis of the SSL Forward Proxy decryption setup,
allowing for the decryption, inspection, and re-encryption of SSL/TLS encrypted traffic to
identify and prevent threats hidden within encrypted sessions.
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
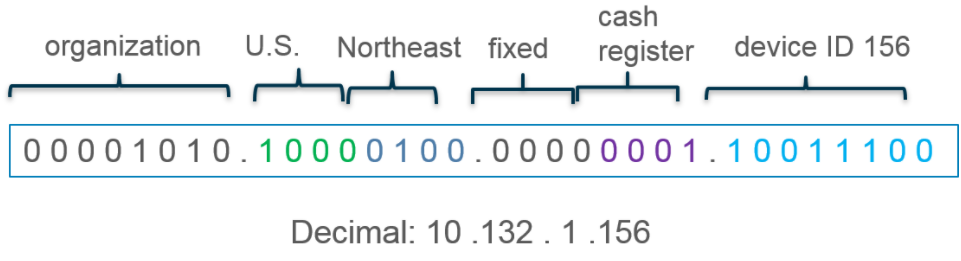
A. IP Netmask
B. IP Wildcard Mask
C. IP Address
D. IP Range
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
A. certificates
B. profiles
C. link state
D. stateful firewall connection
| Page 8 out of 37 Pages |
| Previous |